Difference Between POP3 and IMAP
 POP3
and IMAP are the protocols that are used to retrieve mail from the
mailbox at the mail server to the recipient’s computer. Both are message
accessing agents (MAA). The two protocols POP3 and IMAP are used when
both the sender and recipient of mail are connected to the mail server
by WAN or LAN.
POP3
and IMAP are the protocols that are used to retrieve mail from the
mailbox at the mail server to the recipient’s computer. Both are message
accessing agents (MAA). The two protocols POP3 and IMAP are used when
both the sender and recipient of mail are connected to the mail server
by WAN or LAN.
SMTP protocol transfers the mail from client’s computer to the mail server and from one mail server to another mail server.POP3 has a limited functionality whereas, the IMAP has extra features over POP3.
The basic difference between POP3 and IMAP is that using POP3; the user has to download the email before checking its content whereas, the user can partially check the content of mail before downloading it, using IMAP. Let us check out some more differences between POP and IMAP with the help of comparison chart.
Content: POP3 Vs IMAP
- Comparison Chart
- Definition
- Key Differences
- Conclusion
Comparison Chart
| |||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Post Office Protocol version 3 (POP3) is a message accessing agent (MAA) that transfer the email from mailbox at the server to the local computer of the user. There is a client POP3 software which is installed on the recipient’s computer. The client POP3 software is invoked by the user which thereby creates the connection to the server POP3.
The server POP3 software is installed on the mail server. The connection is made on the TCP port 110. To establish the connection the client has to send username and password for accessing the mailbox. Once the client is authenticated, it can then list and retrieve the emails one by one.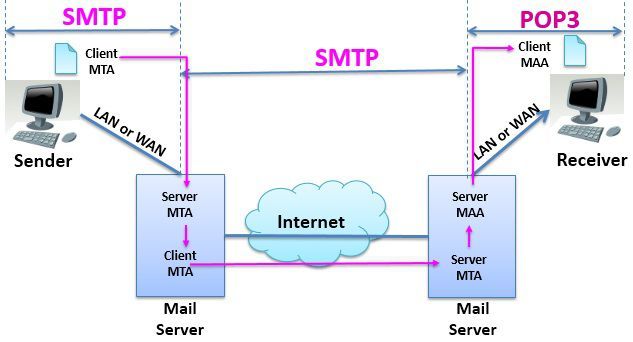 The POP3 protocol operates in two modes, the delete mode and the keep mode. The POP3 protocol operates on delete mode when the user is working on its permanent computer.
In delete mode, once the mail is retrieved from the mailbox it gets
deleted from the mailbox permanently. The mail retrieved from the
mailbox is organized on the user’s computer.
The POP3 protocol operates in two modes, the delete mode and the keep mode. The POP3 protocol operates on delete mode when the user is working on its permanent computer.
In delete mode, once the mail is retrieved from the mailbox it gets
deleted from the mailbox permanently. The mail retrieved from the
mailbox is organized on the user’s computer.
The POP3 protocol operates on keep mode when the user is not working on its permanent or primary computer. In keep mode, the mail remains in the mailbox even after its retrieval. The mail is read by the user, but it is kept in the mailbox for later retrieval and organizing of mail on users permanent computer.
Definition of IMAP
Internet Mail Accessing Protocol (IMAP) is also a mail accessing agent like POP3. But it is more powerful, has more features and is more complex than POP3. The POP3 protocol was found deficient in many ways. So IMAP is introduced to overcome these deficiencies.
POP3 does not allow a user to organize mails on the mailbox. The user can not create different folders on the server. The user can not partially check the content of emails before downloading them. The user has to download an email to read it, in POP.
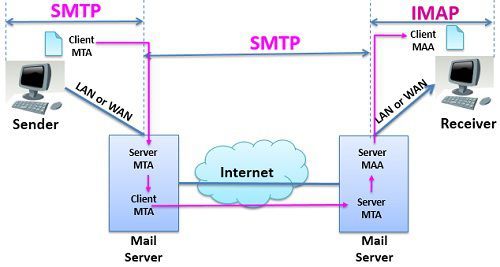
IMAP is used to access the mail from the mailbox at the mail server. Using IMAP the user can check the email header before downloading it. The user is able to check the content of the email for a particular string of character that too before downloading the email.
In case, the bandwidth is limited, using IMAP the user can partially download the mail. It is useful in case the email contains multimedia with high bandwidth requirement. The user can create, delete or rename the mailboxes on the server. The user can also create a hierarchy of these mailboxes in a folder. This is how IMAP is more powerful than POP3 protocol.
Key Differences Between POP3 and IMAP
- The key difference between the POP3 and IMAP is that using POP3 protocol the user has to download the mail before accessing it whereas, using IMAP protocol user can partially check the content of mail prior downloading it.
- Using IMAP protocol user can organize emails on the server which can not be done using POP3.
- Using IMAP protocol the user can create, delete or rename the mailboxes, even the user can create a hierarchy of mailboxes in the folder, but it is not possible using POP3.
- POP3 protocol does not allow you to search the content of mail for a particular string of character prior downloading whereas, using IMPA user can search the content of an email for a specific string of character before downloading.
- IMAP allows a user to download the mail partially in the case of limited bandwidth. However, this function is not available in POP3.
- POP3 is simple and has limited functionality whereas, IMAP is powerful, complex and have extra functions over POP3.
Conclusion
Bothe POP3 and IMAP are the message accessing protocols. But IMAP is more powerful and has many advanced features over POP3.
Comments
Post a Comment